In today’s digital age, where privacy and data security are paramount, it is crucial for both website owners and users to understand the significance of these protocols. Learn the key features and benefits of HTTPS and SSL Certificates, shedding light on how they contribute to encrypted, authenticated, and tamper-resistant data exchange over the internet. Explore the world of secure online connections and discover why implementing HTTPS and SSL is not just a best practice but a necessity for a safer online experience.
What is an SSL certificate?
An SSL (Secure Socket Layer) certificate plays a crucial role in establishing secure and encrypted communication between a user’s browser and a website’s server. It authenticates the identity of the website, ensuring users connect to the intended and legitimate site, and enables encryption to safeguard sensitive information during transmission. Additionally, the certificate contributes to data integrity by preventing tampering or alteration of information in transit. Visual cues such as a padlock icon in the browser’s address bar or a URL starting with “https://” signify the presence of SSL certificates, instilling trust and confidence in users and indicating a secure online connection. Trusted Certificate Authorities (CAs) issue these certificates, and website owners install them on their servers to enhance security, especially for websites handling confidential data like login credentials or conducting financial transactions.
Free SSL Certificate Options
Various Certificate Authorities (CAs) and services that provide free SSL/TLS certificates allow you to obtain a free SSL certificate. These certificates are suitable for securing websites and ensuring encrypted communication. When you consider free SSL certificates, remember that they typically represent domain-validated (DV) certificates, verifying only the ownership of the domain. For higher levels of validation (organization or extended), you might need to explore paid options. Moreover, many web hosting providers integrate solutions for free SSL certificates through services like Let’s Encrypt, so consult your hosting provider to check for available options. Always ensure that the CA or service you choose is reputable and trustworthy.
Let's Encrypt
Let's Encrypt is a widely used and respected CA that provides free SSL certificates. They offer automated certificate issuance and renewal processes. Many hosting providers have integrated Let's Encrypt, making it easy to enable SSL for your website.
Cloudflare
Cloudflare provides a free SSL certificate for websites using their content delivery network (CDN). It offers a flexible SSL option, which allows you to enable SSL with minimal configuration.
SSL For Free
SSL For Free is a service that allows you to generate free SSL certificates. It uses the ACME protocol and can be a good option for those who want a straightforward way to obtain SSL certificates.
ZeroSSL
ZeroSSL is another service that offers free SSL certificates. It provides a user-friendly interface for certificate generation and renewal.
What is a self signed SSL certificate?
An entity generates and signs a self-signed SSL (Secure Socket Layer) certificate for its own use, instead of involving a Certificate Authority (CA). In simpler terms, a website or server creates its own certificate without relying on a third-party CA. Although self-signed certificates offer encryption, they lack the validation and trust associated with certificates signed by a reputable CA. While self-signed certificates find use in specific cases, particularly in controlled environments or for testing purposes, it is crucial to emphasize that they do not adequately replace CA-signed certificates in production environments, where trust and validation are of utmost importance. For publicly accessible websites, the standard practice to ensure security and build user trust is obtaining a certificate from a trusted CA.
Key characteristics of self-signed SSL certificates include:
No Third-Party Verification
Self-signed certificates do not undergo the validation process performed by CAs. This means there is no external verification of the entity's identity, and users have to rely solely on the entity's assurance.
Encryption
Self-signed certificates still enable encryption of data during transmission between the user's browser and the server. This ensures the confidentiality of information exchanged.
Browser Warnings
When users access a website using a self-signed certificate, web browsers typically display warning messages. These warnings inform users that the certificate is not issued by a trusted CA, and users must decide whether to proceed or not
Good for Development Environments
Self-signed certificates are often used in testing or development environments where the focus is on encryption rather than validation. They provide a way to secure communication without the need for a CA.
Bad for Public-Facing Websites
Due to the lack of third-party validation, self-signed certificates are not recommended for production or public-facing websites. Users may be hesitant to trust such certificates, and the warnings from browsers can deter visitors.
Manual Certificate Management
Self-signed certificates require manual management, including generating, installing, and renewing them. They do not benefit from the automatic renewal processes provided by reputable CAs.
What is the difference between http and https?
Both HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) serve as protocols for communication over a computer network, specifically the World Wide Web. The primary distinction between them is the level of security they offer. While both facilitate the exchange of data between a user’s browser and a website, HTTPS enhances security by encrypting the data, ensuring data integrity, and authenticating the website’s identity. Consequently, organizations prefer HTTPS for secure communication, particularly when handling sensitive information like login credentials or personal details.
HTTP
- Security: It operates over a plain text connection, implying that it does not encrypt the data exchanged between the user’s browser and the website. This absence of encryption exposes it to eavesdropping and data tampering. Attackers can intercept and read any information transmitted via HTTP.
- Data Integrity: As it doesn’t offer encryption, it provides no assurance of data integrity, allowing for undetected alterations to the data during transmission.
- Authentication: It lacks authentication of the website’s identity, making it vulnerable to man-in-the-middle attacks, wherein a malicious actor can impersonate the intended website.
- URL Scheme: It uses the URL scheme “http://”.
HTTPS
- Security: It employs SSL/TLS (Secure Socket Layer/Transport Layer Security) protocols to encrypt the data during transmission. This encryption guarantees that third parties cannot easily intercept or manipulate the information exchanged between the user and the website, ensuring its security.
- Data Integrity: SSL/TLS ensures data integrity, detecting any tampering that may occur during transmission. In such cases, the system will alert the user or terminate the connection.
- Authentication: SSL/TLS certificates are instrumental in authenticating the identity of the website, providing users with assurance that they are communicating with the intended and legitimate website.
- URL Scheme: It uses the URL scheme “https://”.
How to redirect http to https
To redirect HTTP to HTTPS, configure your web server to automatically forward users from the non-secure (HTTP) version of your website to the secure (HTTPS) version. The specific steps may vary depending on the web server software you are using. Here are general instructions for some common web servers (always backup your configuration files before making changes):
Apache Web Server:
- Open your Apache configuration file. This file is often named httpd.conf or apache2.conf.
- Locate the Virtual Host configuration for your website.
- Add the following lines to redirect HTTP to HTTPS:
<VirtualHost *:80>
ServerName yourdomain.com
Redirect permanent / https://yourdomain.com/
</VirtualHost>
Replace yourdomain.com with your actual domain.
- Save the changes and restart the Apache server.
Nginx Web Server:
- Open your Nginx configuration file. This file is often named
nginx.confor is located in the/etc/nginx/sites-available/directory. - Locate the server block for your website.
- Add the following lines to redirect HTTP to HTTPS:
server {
listen 80;
server_name yourdomain.com;
return 301 https://$host$request_uri;
}
Replace yourdomain.com with your actual domain.
- Save the changes and restart the Nginx server.
Microsoft IIS:
- Open IIS Manager on your Windows server.
- Select the site you want to configure.
- In the Actions pane, click on “HTTP Redirect.”
- Check the box for “Redirect requests to this destination” and enter https://yourdomain.com/ in the box.
- Ensure the boxes for “Redirect all requests to exact destination” and “Only redirect requests to content in this directory (not subdirectories)” are checked.
- Click “Apply” to save the changes.
What is HSTS? (HTTP Strict Transport Security)
HSTS, a web security policy mechanism, actively protects websites against man-in-the-middle attacks, including protocol downgrade attacks and cookie hijacking. Its design revolves around enforcing secure connections by instructing web browsers to exclusively interact with a website over HTTPS (HTTP Secure) rather than HTTP.
It’s crucial to emphasize that once a website sends the HSTS header to a user’s browser, the browser automatically enforces HTTPS for subsequent visits to that site for the specified duration. This enforcement persists even if the user manually enters “http://” in the address bar. HSTS actively enhances the security of web communications, proving particularly beneficial for websites handling sensitive information.
Key features of HSTS include:
Forcing HTTPS
When a website implements HSTS, it sends an HSTS header to the user's browser. This header informs the browser that it should only connect to the website using the secure HTTPS protocol for a specified period of time.
Preventing Downgrade Attacks
HSTS helps prevent man-in-the-middle attacks where an attacker attempts to downgrade a secure HTTPS connection to an unencrypted HTTP connection. This enhances the overall security of data transmitted between the user's browser and the website.
Cookie Security
By ensuring that communication with the website is exclusively over HTTPS, HSTS helps protect sensitive information, such as session cookies, from being intercepted or manipulated by attackers.
Improved User Security
HSTS provides an additional layer of security for users by automatically redirecting them to the secure version of the website, even if they initially attempt to connect via HTTP. This reduces the risk of users inadvertently accessing the non-secure version of the site.
Header Implementation
Websites implement HSTS by including the "Strict-Transport-Security" header in their HTTP responses. The header includes directives such as "max-age," which specifies the time (in seconds) for which the browser should enforce the use of HTTPS, and "includeSubDomains," which indicates that all subdomains should also use HTTPS.
How to implement HSTS Headers
Implementing HSTS involves configuring your web server to include the HSTS header in its responses. Here’s a general guide on how to implement HSTS on a variety of servers and hosting providers:
Apache Web Server:
- Enable the mod_headers module: Make sure that the mod_headers module is enabled in your Apache server.
sudo a2enmod headers
sudo systemctl restart apache2 - Configure HSTS: Edit your Apache configuration file (usually located in /etc/apache2/sites-available/ or /etc/httpd/conf.d/). Add the following lines within the <VirtualHost> section for your domain:
<VirtualHost *:443>
# ... other configurations ...Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
</VirtualHost>
- max-age: The time, in seconds, that the browser should remember to only access the site over HTTPS (one year in the example).
- includeSubDomains: Optional, enforces HSTS for all subdomains.
- preload: Optional, indicates that the domain should be included in the HSTS preload list.
- Restart Apache: After making changes, restart Apache to apply the configuration.
sudo systemctl restart apache2
Nginx Web Server:
- Configure HSTS: Edit your Nginx configuration file (usually located in /etc/nginx/sites-available/ or /etc/nginx/conf.d/). Add the following lines within the server block for your domain:
server {
listen 443 ssl;
# ... other configurations ...add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";
}- max-age, includeSubDomains, and preload have the same meanings as in Apache.
- Restart Nginx: After making changes, restart Nginx to apply the configuration.
sudo systemctl restart nginx
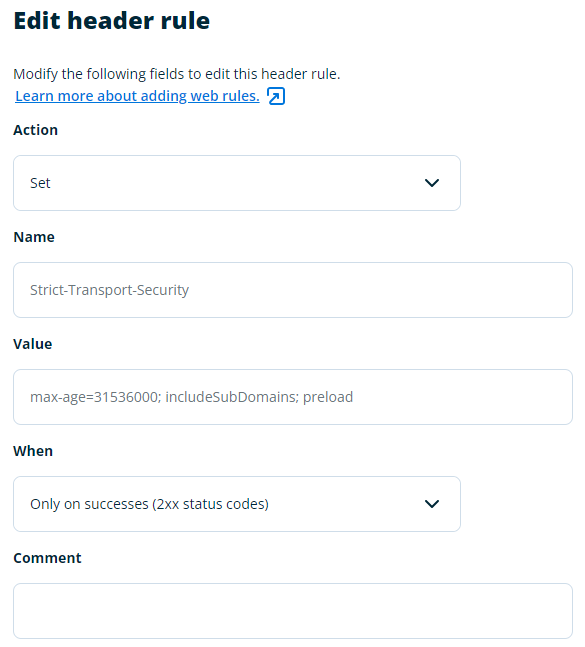
WP Engine:
- Login to WP Engine and go to Web Rules.
- Click Enable Web Rules (if not already enabled) then select Header Rules.
- Set the following values:
- Action: Set
- Name: Strict-Transport-Security
- Value: max-age=31536000; includeSubDomains; preload
- When: Only on Successes (2xx status codes)
Testing:
After implementing HSTS, you can check whether it’s working by visiting your site and checking the response headers using browser developer tools or online tools like SecurityHeaders.com. You should see the Strict-Transport-Security header with the specified values.
Note: Before enabling HSTS, ensure that your website works correctly over HTTPS, as HSTS enforces HTTPS for the specified duration, and browsers will remember this policy.
Your website's safety is our priority.
Don’t navigate these complexities alone—reach out to us for expert guidance and secure your digital fortress today.